The scam starts with an email asking the user to update their email settings according to the linked instructions. The URL in the message brings the user to a Google Groups page linking to a malicious download.
Sample Email:
The link on the Google Groups page is a Downloader Trojan with better than normal virus detection. 58% of virus scanners detected the file as malicious on Virus Total.
The Downloader then does its job, downloading a mixed bag of malware from several locations. eSoft is currently blocking all known distribution points. Among the malware downloaded is Desktop Security 2010, a Rogue Anti-Virus program.
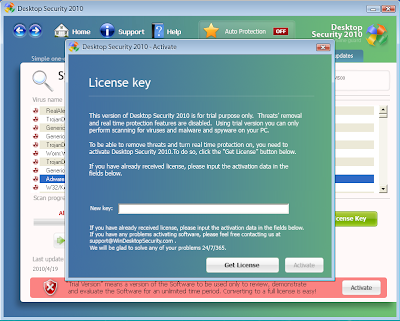
A fake system scan is run notifying the user they’ve been infected and prompting the user to purchase a license key to remove the malware.
For only $89.95 you can get a lifetime license with special support. Users following through on the purchase have handed their credit card and other personal information to cybercriminals on a silver platter.
Access to the Internet through the browser is blocked until you’ve purchased a license, adding a hint of Ransomware to the mix. Between this tactic and the official looking interface, unsavvy users are unfortunately easy prey.
Use of community sites like Google Groups, Windows Live, Blogger and others is becoming commonplace for cybercriminals looking to get the upper hand on web and spamfilters. Secure Web Filtering with a combination of granular classifications and real-time URL lookups is the most effective way to combat these threats.
eSoft is actively identifying and flagging select Google Groups pages as Compromised as they’re discovered. Other sites involved with this attack are blocked as Malware Distribution Points.
Update: May 12th 10:00 AM
It appears the spammers have switched tactics and are now sending fake ecards claiming to be from 123greetings.com. Users receive an email in the form below with an image link. The links in the email use the same Google Groups URLs and present the same dangerous malware. This new round of spam uses an even more effective social engineering trick than in the first campaign, and more unsuspecting users will certainly fall victim.





No comments:
Post a Comment