If you follow the Threat Center Blog, you’ve heard us talk about “Rogue AV,” but may not fully understand what we’re referencing. This post is for those users who are not already familiar with this widespread and common threat.
In short, when we and other security researchers reference Rogue AV, we’re referring to an Internet scam where an official-looking web page pops up telling the user that a virus has been detected on their computer. The web page often appears to be scanning the local computer and often reports multiple found infections. The web page, the report, and everything about this scam is a fraud.
Millions of users have been duped into installing malicious software, also known as malware onto their systems allowing cybercriminals to steal money and other personal details. Here’s how the attack works:
Step One: Get the user to the malicious website
First, the group or groups behind these attacks first post large numbers of links to some new domain by spamming community forums, blog comments, and by putting the links inside hidden elements on compromised websites in a technique known as
Blackhat SEO (Search Engine Optimization). In this way, they are able to get the target website high up in search results for common or recently trending search terms. Right now, for example, search results on Wimbledon and the World Cup are actively being poisoned in this manner.
The above technique is usually seen in conjunction with one or more of the following:
- Redirects from compromised websites that are otherwise legitimate
- Spam emails that are often sent via other compromised computers
- Malvertisements where attackers pay for an ad in a legitimate ad network, but use the ad to send people to the malicious website. In the past year, reputable sites like the New York Times, White Pages, Tech Crunch and others have been caught hosting such malvertizements.
Step Two: The con game
Once on the website, social engineering tricks are invoked to convince a user to fall for this modern Internet con. Computer users are conditioned with constant reminders to keep their computer free from virus and malware by running anti-virus software and keeping their virus definitions up to date. These websites use this conditioning against the user, using visual elements to establish authority and trust and then causing a sense of danger and urgency when notifying the user that their computer is infected with viruses and that their data personal computer is under someone else’s control.
Rogue anti-virus malware comes in many different forms and will take different approaches to fool a user, but at the most basic level, rogue anti-virus scams convince the user that they have a problem and that they need to download some software to fix the problem.
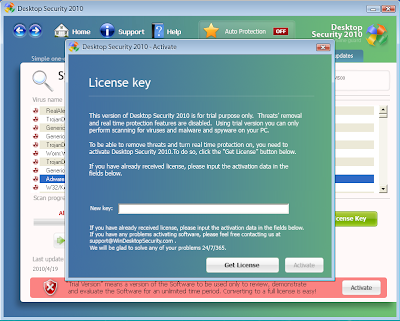
The screenshots below are just a few examples of fake scanners. These specially crafted pages are made with great detail to look exactly like Windows XP, Vista, or Windows 7 system alerts.
Fake scans like these are very believable for uneducated users and lead to a very high success rate for cybercriminals.
Step Three: Infection
Frequently a box pops up that asks the user if they want to download the software that will fix the purported problem. In many cases, it doesn’t matter if the user agrees or cancels, the download will begin in either case. Once the downloaded file is opened, the system is infected and the user has been tricked into installing the very thing he or she sought to remove.
Cybercriminals make it very difficult to click away from the page, so that in some cases, the user relents out of a sense of frustration and not knowing how else to move forward. In many cases the malicious file is downloaded with no user interaction at all.
The actual file that is downloaded changes often with different names and characteristics. eSoft rarely sees more than two or three legitimate anti-virus software (of over 40 checked) detecting the file as a virus at the time of the attack. The perpetrators of this attack spit out new variations on the download at a very high rate in an attempt to stay ahead of signature-based anti-virus software.
Step Four: Asking for payment
Once a user has clicked to open the malicious file and install the software, the problem only gets worse. The cybercriminals do well in masking their malicious intentions throughout the install process. In many cases the installation is a
silent install – one which requires no user interaction – or a standard install wizard which raises no red flags to the user.
Once installed, the rogue anti-virus program will inundate the user with notifications that the system is infected and that they still need to take action. In order to remove the supposed infections (not the real problem) the user is asked to pay a license or subscription fee that typically runs between $50 and $100 USD.
Though the branding changes – these screenshots show the Rogue AV “Alpha AntiVirus” – the checkout pages remain as convincing as the rest of the scam, frequently with badges showing secure payments and other “trust me” icons. Pricing is comparable to legitimate anti-virus products and comes with a money back guarantee to further convince the user who may be wavering that the risk to giving up their credit card and personal information is low. In reality, submitting credit card info does not clean their system, but instead sends name, address, and credit card info directly to the perpetrators of the attack.
Users infected with this might just assume this is an annoyance, but the scam goes much deeper than this. These programs have been created by large underground crime rings that now have the users’ personal information and credit card number. In addition, these programs are often packaged with downloader Trojans which are capable of downloading any type of malware the attacker chooses. Because many of these criminal enterprises are also heavily involved in banking malware this is just one of the many additional types of malware that can be installed. As a result, an infected computer should have a computer professional remove the virus, which can cost small businesses thousands of dollars per year.
Prevention
Cybercriminals go a long way to making sure they can infect a machine and to get around classic signature-based virus scanning. If a user gets a web browser window that says their computer is infected with malware, they should immediately attempt to close the window. If that is not possible, then quitting and restarting the web browser is the next best thing. This, of course, requires that users are trained in spotting and avoiding this attack, but in practice, training unsavvy users alone is not always fruitful.
Now more than ever, malware is distributed via the web. In fact, over 75% of new malware is delivered through the web. Classic anti-virus is struggling to address these threats effectively. The most effective way to stop web-based threats is with
Secure Web Filtering. Secure web filtering works by detecting and blocking dangerous sites even before there is any anti-virus protection. By blocking access to the site, the threat is mitigated. Secure web filtering must have real-time updates in order to block these fast moving websites, but with such a solution, users should be well protected from this pervasive threat.